
Home » Identity and Access Management What Teams Often Get Wrong


Many enterprise teams treat identity and access as if they are the same thing. They aren’t. Identity confirms who a user is. Access defines what that user is allowed to do. Assuming that an authenticated identity automatically deserves access is one of the most common—and costly organizational security mistakes.
Flexible work environments, remote access, and after-hours system use have made this problem worse. Even with identity and access management (IAM) programs in place, enterprises often grant too much access that later result into financial losses.
Gartner has repeatedly highlighted that breaches frequently occur not because identities are missing, but because access is poorly governed.
This blog discusses the major gaps in an organization’s IAM security and how correcting identity vs access management misunderstanding strengthens enterprise security.
In most organizations, identity and access are often treated as the same thing, but they answer two very different questions. Teams often assume that once someone is verified, they can be trusted with everything related to their role. Which is not true.
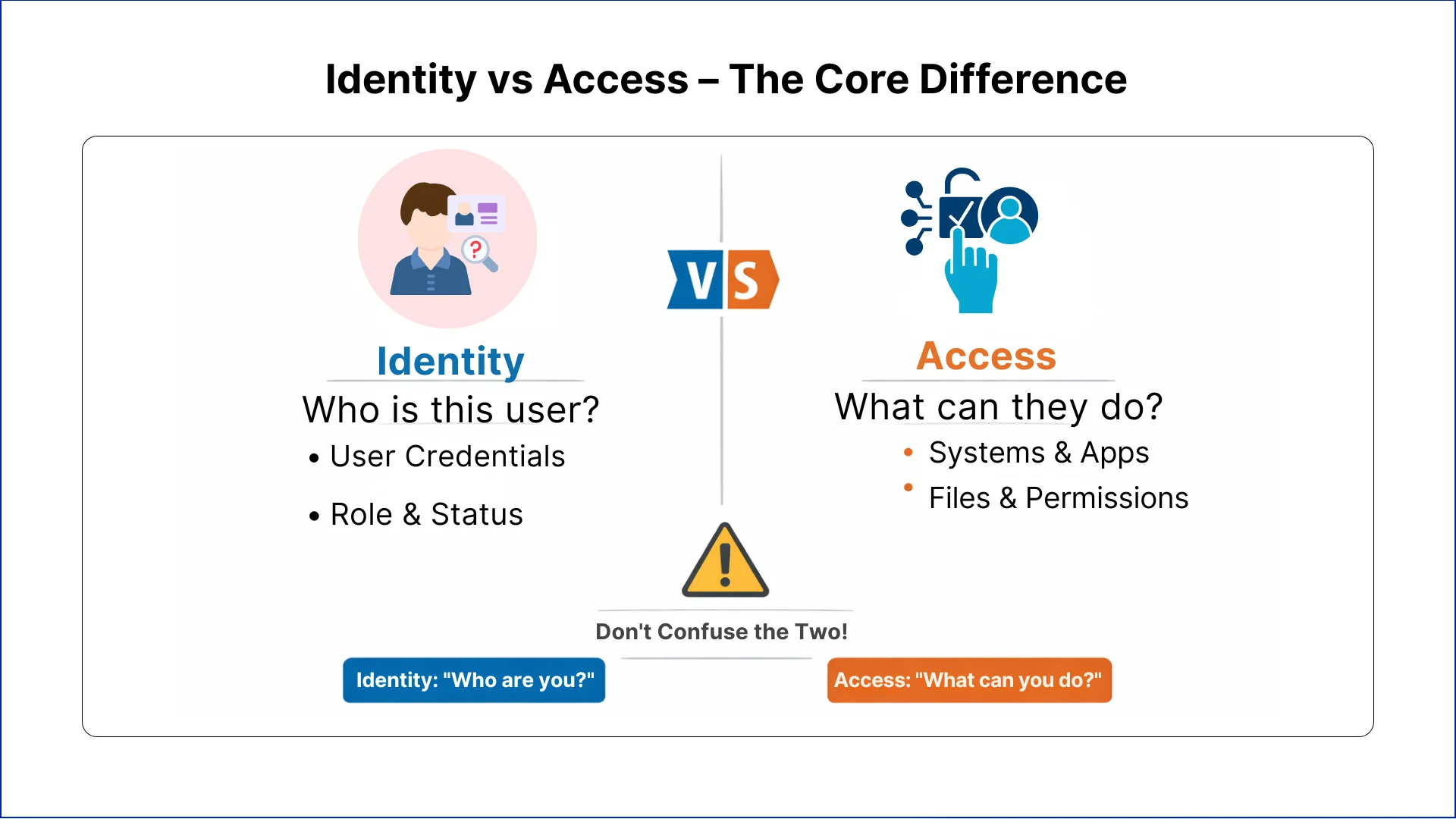
Access answers the question: What is this person allowed to do? It defines which systems, files, and functions the person can use.
Identity management security focuses on making sure the right people are correctly identified. Access management ensures they only do what they need to do. Confusing these two leads to errors that are often invisible until something goes wrong.
Get free Consultation and let us know your project idea to turn into an amazing digital product.
Even organizations with strong IAM programs often make simple mistakes. These mistakes are usually about processes, not technology.
To speed up onboarding or reduce internal requests, many teams grant broader access than necessary. The thinking is practical. It avoids delays and future approvals.
Over time, this practice creates users who can:
IAM security suffers when access is given for convenience rather than actual need. What starts as a time-saving step becomes a long-term problem.
Employees move between teams, get promoted, or take temporary assignments. Many enterprises add new access but forget to remove old permissions.
This leads to:
Identity may remain correct, but access no longer reflects what the person should be able to do. This mismatch is one of the most persistent IAM mistakes enterprises make.
Temporary workers and contractors often receive the same access as permanent staff. When contracts end, accounts may remain active.
This allows:
Treating temporary staff like permanent employees is one of the easiest ways IAM security fails.
Some teams assume that if a person has a senior position or long tenure, they can be trusted with broad access. This is common but risky.
The result is:
Access should be based on actual responsibilities, not assumed from a job title.
When employees leave, removing access is often delayed. Accounts may remain active for days or weeks because of slow processes.
This exposes the organization to:
IAM compliance expects access to be removed immediately when someone leaves.
IAM is often owned only by IT. Business teams, HR, and security teams are frequently not involved.
This creates problems like:
IAM works best when multiple teams share responsibility. Identity and access management is not only technical; it is operational.
When identity or access management are managed incorrectly, the consequences may not be immediately visible, but they build up over time.
Treating identity and access as the same makes both security and compliance harder to manage.
Share your project idea with us. Together, we’ll transform your vision into an exceptional digital product!

Effective IAM security comes from actively managing identity and access in a way that reflects actual work responsibilities. It is not about installing tools; it is about aligning access with real business needs.
Each user’s access should match their role. Employees should only have permissions for the systems and data they need. Granting extra access for convenience or future needs increases risk and creates hidden security problems. Access should change as responsibilities change, ensuring identity and access are always aligned.
2. Review Access Regularly
Access must be reviewed at regular intervals. These reviews ensure that permissions still match work responsibilities. Managers, system owners, and security teams should verify that access is appropriate and remove anything unnecessary. Regular reviews prevent access from accumulating over time, keeping IAM security effective.
3. Remove Access Immediately When Not Needed
When employees leave, change roles, or finish temporary assignments, access should be revoked right away. Delayed removal leaves systems exposed and increases the risk of unauthorized activity. Immediate removal simplifies compliance and keeps enterprise systems secure.
4. Handle Privileged Access Separately
High-level permissions require special attention. Administrative accounts should be granted only, when necessary, monitored regularly, and reviewed separately from standard accounts. Treating privileged access the same as regular access increases exposure and complicates audits.
5. Make IAM a Shared Responsibility
IAM security should involve IT, business leaders, HR, and security teams. Shared responsibility ensures that access decisions consider business context, role changes are captured correctly, and accountability is clear. Collaboration improves speed, accuracy, and compliance.
6. Support Zero Trust Practices
Zero trust assumes no one should have access by default. IAM security should check and approve access continuously, monitor changes, and prevent unnecessary permissions. Correctly managed IAM supports zero trust without slowing operations, giving organizations control over who can do what.
In regulated environments, simply knowing who someone is does not guarantee security. Identity management without proper access controls leaves organizations exposed to risks such as over-privileged accounts, insider threats, and compliance failures.
Teams must focus on both identity and access management, ensuring that users have the right permissions for their roles at all times.
When identity and access management is handled correctly, employees see only what they need, sensitive systems remain secure, and compliance requirements are consistently met. IAM security becomes a strength, not a risk, giving teams confidence that their organization is safe.
IAM is a security framework that verifies user identities and controls their system permissions. It ensures the right people access appropriate resources at the right time, protecting sensitive data through authentication and authorization controls.
No, they serve distinct functions. Identity management confirms who users are through authentication, while access management determines what they can do through authorization. Both components work together within IAM security frameworks.
Identity management validates user credentials and maintains user profiles. Access management enforces permissions based on roles and responsibilities. Identity answers “who are you” while access controls “what can you do.”
Identity management authenticates users first, then access management applies authorization rules. This sequential process ensures verified identities receive appropriate permissions, creating layered security that prevents unauthorized actions even from authenticated users.
No, authentication alone creates security gaps. Verified identities without controlled permissions lead to over-privileged accounts and compliance failures. Effective IAM requires both components to enforce least privilege and protect enterprise resources.
Delayed access revocation creates security vulnerabilities and compliance violations. Former employees can leak sensitive data, access confidential systems, or compromise accounts. Immediate deprovisioning upon termination prevents unauthorized access and audit findings.
PAM specifically controls high-level administrative permissions requiring extra security measures like session recording and just-in-time access. IAM governs standard user permissions across the organization, while PAM adds specialized controls for elevated privileges.
Contractors have temporary relationships requiring time-bound permissions and stricter monitoring. Unlike employees, their access should automatically expire with contract end dates, preventing persistent accounts that create compliance gaps and security risks.
IAM enforces continuous verification and least privilege access central to zero trust architecture. It validates every access request regardless of network location, monitors behaviour patterns, and revokes permissions dynamically based on risk signals.
Quarterly reviews catch permission creep before it becomes problematic. High-risk accounts need monthly audits, while privileged access requires continuous monitoring. Regular reviews ensure permissions align with current responsibilities and prevent unauthorized access accumulation.

Have a one on one discussion with our Expert Panel

When discussions turn to hybrid and native app performance, Ionic is often the framework that gets questioned. Among cross-platform options such as React Native, Flutter, and Xamarin, the Ionic UI framework is known for helping teams get a mobile app to market faster. However, this speed is often viewed as a compromise on performance.

Selecting the right database is one of the most significant decisions in modern application development. Whether you are building a startup product, scaling an enterprise system, or designing cloud-native architecture, the debate around sql vs nosql continues to be highly relevant. The database you choose directly impacts performance, scalability, data consistency, and long-term maintenance.

While companies invest in flutter app development for interactive user interfaces, an app’s performance often becomes the deciding factor in whether users stay or leave. Users may not consciously notice a well‑designed interface, but they immediately feel when an app becomes laggy, slow, or unresponsive.

Founder and CEO

Chief Sales Officer
